TxSSC
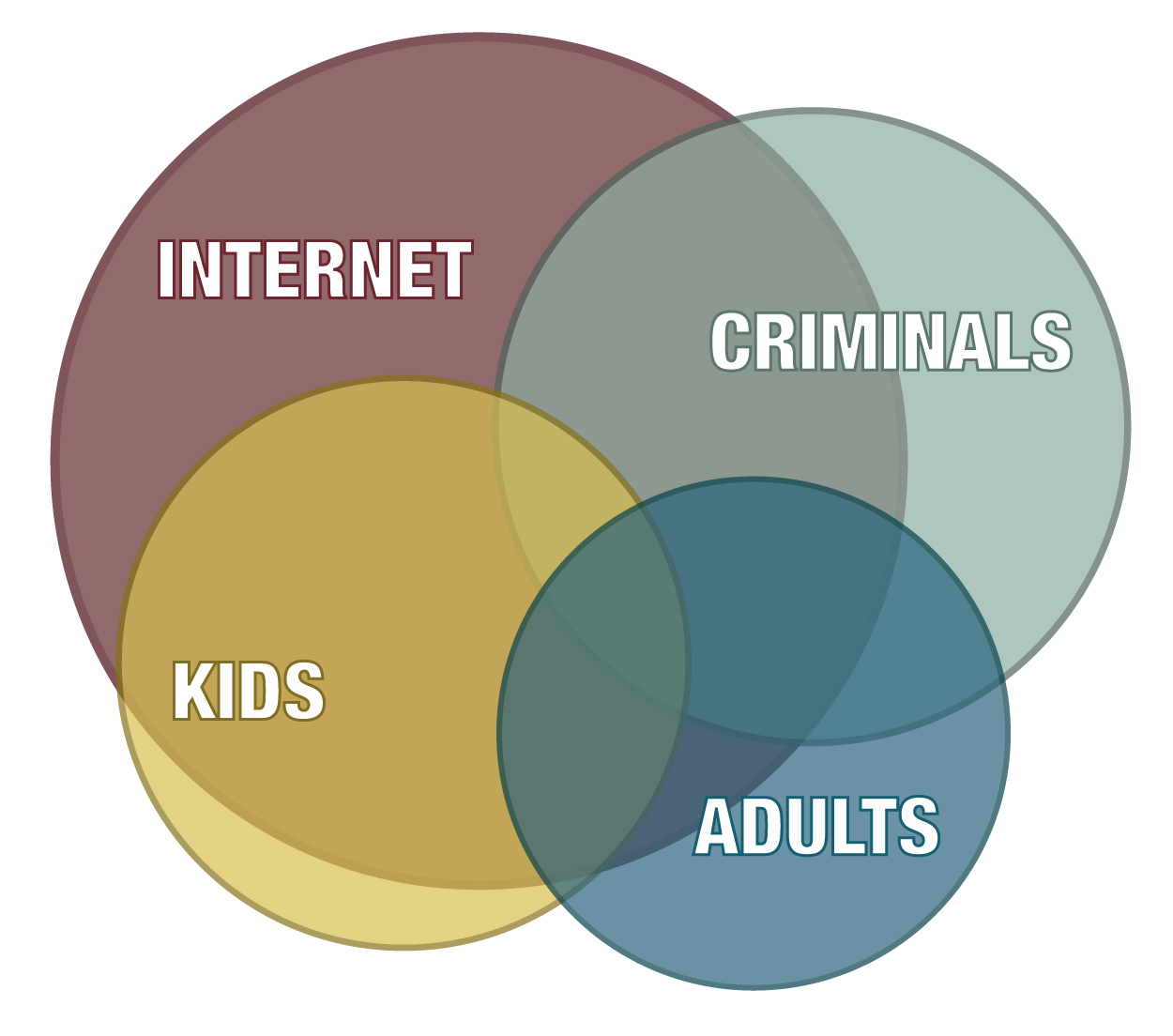
When technology is combined with people having no consequences, training, or life experience, then crime and victimization can run rampant. We will discuss this in more detail later, but you need to be aware from the start of this course that there is a robust framework of laws addressing bullying, sexting, revenge porn, and sextortion that were created to protect you and to explain that dangerous online behavior is often clearly illegal.
Not everyone views the internet and social media the same way. For purposes of this online course, we will refer to three groups of people:
- Young people (ages 12 through 18)
- Adults
- Predators (consisting of both young people and adults)
This module examines types of cyber predators and how adults and young people view internet concerns differently. It also covers how you can help protect yourself from cyber predators.
Objectives
(translation: potential test questions)
At the end of this module, students should be able to:
- Recognize the common characteristics of cyber predators.
- Contrast how adults and young people view the internet differently.
Topics
This module will review the following topics:
- Types of cyber predators
- Human trafficking
- Adults and young people
- Social engineering